Introduction
Users are urged to create unique and complex passwords every time they sign up for an online service or tool. Strict password policies and the sheer number of credentials lead to increased password fatigue.
Users are resorting to unsafe practices, such as:
- Using the same credentials for multiple accounts.
- Creating weak passwords.
- Writing down and storing unencrypted credentials.
- Using slight password variations for different accounts.
The Single sign-on (SSO) concept takes some pressure off users and reduces the number of passwords they need to create and remember.
Learn how SSO works and streamline the login process for internal tools or customer-facing apps.

What is SSO (Single Sign-On)?
SSO is an authentication scheme that allows users to access separate applications using the same credentials.
Once a user enters their login information for one app, they can access other trusted and preconfigured applications without re-entering their credentials.
The different applications must enter a trust relationship beforehand to verify and authenticate the user’s digital identity. Organizations typically use third-party identity providers to automate and expedite the authentication process.
Implementing single sign-on allows businesses to:
- Improve the employee or customer login experience.
- Reduce password fatigue.
- Enable staff to extend workflows across devices and apps more easily.
- Centralize user access controls.
- Streamline audit trail analyses.
Single sign-on solutions are usually part of a broader Federated Identity Management (FIM) system.
A Short SSO Glossary
- Federated Identity Management (FIM) - Two or more separate domains or organizations interlink their authentication systems via a third-party identity provider (IdP). Domains that have established an FIM relationship trust the authentication process conducted on the other federated domains. Users can access services within an FIM network without re-entering login details or further authentication.
- Identity Provider - An identity provider (IdP) is a third-party service that stores and manages digital user identities and facilitates access control among federated service providers.
- Service Provider - A remote application that relies on the identity provider to confirm that the user was successfully authenticated.
- Entities - An entity is a unique object (process, client, server, or resource owner) participating in the authentication process.
- Web Endpoint - A URL that allows web clients to communicate and interact with a specific web service.
- Issuer - The issuer authenticates data and issues an authentication message.
- Same Sign-On - The user can utilize the same credentials to access different services, but they must enter their credentials for each service. The authentication process is not automated as with single sign-on.
- OAuth - OAuth is an authorization framework that enables applications to share data and resources with other apps without disclosing the user’s password. The permissions and scope depend on the resource owner’s consent.
- OpenID Connect (OIDC) - OpenID Connect is an identity protocol that allows clients to verify the user’s identity and obtain basic profile information about authenticated sessions and users.
- Security Access Markup Language (SAML) - SAML is an XML-based open-standard for exchanging authentication and authorization data between an identity provider (IdP) and service providers.
- Token-based authentication - A server generates a unique encrypted token based on the user’s credentials and data. The token is subsequently used to authenticate the customer with other applications and service providers. The user can utilize the encoded token for authentication purposes instead of sharing sensitive data such as usernames or passwords.
Note: Learn about curl basic auth, an authentication method in which the server declares that the client must submit a username and password.
How Does SSO Work?
SSO solutions use different frameworks and protocols to establish a trusted relationship between authentication systems and service providers. The authentication flow depends on the organization’s resources and business model requirements.
Single sign-on relies on authentication tokens to transfer authentication-related data between applications:
- The Identity Provider tokenizes the user’s data and sends the token to the Service Provider to confirm that the user was successfully authenticated.
- The token is digitally signed and contains a certificate that confirms the token was sent from a trusted source, i.e., the Identity Provider.
- The Service Provider accepts the token certificate and uses it to identify and grant access to a particular user.
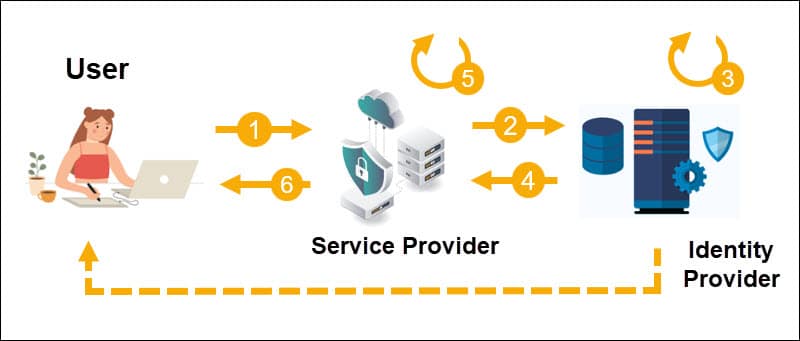
The following steps illustrate a typical SSO authentication flow:
- The user tries to access an application hosted by the Service Provider.
- The Service Provider collects the user’s data and sends a token to the Identity Provider. The token contains basic user data and is part of a request to authenticate the user.
- The Identity Provider checks if the user has already been authenticated, in which case the user is granted immediate access. If the user cannot be authorized, they must enter the credentials stored with the Identity Provider. This may include a password, one-time password, or other authentication methods.
- Once the Identity Provider validates the provided credentials, it sends a token back to the Service Provider to confirm that the user was successfully authenticated.
- The Service Provider receives and validates the token based on the trust relationship set up between the Identity Provider and Service Provider.
- The user can access the application hosted by the Service Provider.
The same authentication flow is applied if a user tries to access a different application within the FIM.
Is SSO More Secure?
SSO allows organizations to centralize access control, oversee audit logs, and decrease the number of security issues caused by password mismanagement.
Customers and employees use fewer passwords which reduces the potential attack surface and the risk of accidental or deliberate password sharing.
However, the underlying risks for password-based and token-based authentication are still present.
Advanced persistent threats (APT) that include cross-site scripting (XSS) attacks and session hijacking are a considerable threat to applications using SSO.
If an attacker manages to hijack the token session, they can potentially access all services within an FIM.
Businesses that deal with sensitive customer data must introduce additional authentication tools like two-factor authentication.
Single sign-on can reduce costs associated with lost passwords, account creation, and access issues, but organizations may need to invest additional resources to develop and implement SSO solutions.
SSO increases password security while improving customer satisfaction and allowing employees to complete everyday tasks more efficiently.
Conclusion
You know how SSO works and the benefits it can bring to your customers and employees.
Passwords are free, easy to scale, and users understand how they work. However, apps and online services are becoming more capable and immersive and, as such, are changing user expectations and behavior.
Users want a fast and seamless login that includes passwordless authentication and IoT interoperability, and SSO is an important steppingstone.
