Introduction
The online environment and the digital channels used are closely monitored by hackers, data thieves, and other malicious computer pundits. To prevent major data breaches, organizations opt for two-factor identification.
By requiring their clients and employees to enter a password and an additional code or token during transactions, organizations significantly reduce the risk of their computer systems and company data being hacked.
The simple protection mechanism provided by two-factor authentication systems is an invaluable asset for corporations, small and mid-sized businesses, as well as for individuals making payments or receiving money on the Web.
This article explains what two-factor authentication is, how it works, and how it secures online payments.

Two-Factor Authentication Definition
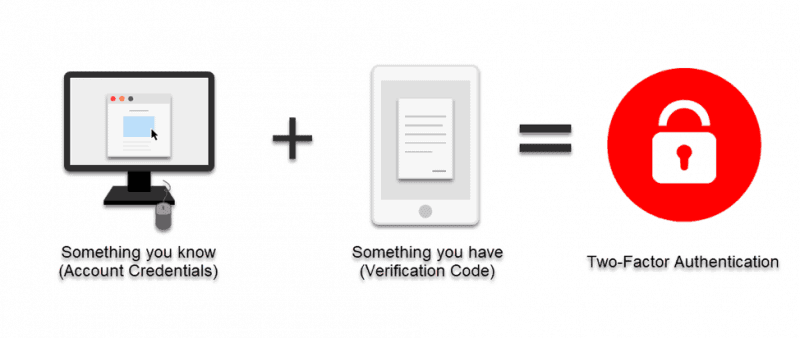
Two-factor authentication is a security verification stage of payment processing during which users confirm their identity with something they know (a password) and something they possess (a code, a one-time password, or a token). Two security layers guard the account for added security.
As opposed to 2FA, single-factor authentication uses just a username/password combination for securing access. Even though usernames and passwords are still important elements of online authentication, now they’re accompanied by some additional security elements, with which they make two-factor authentication.
How Does Two-Factor Authentication Work
Two-factor authentication is based on three main principles:
- User’s knowledge. A password or a secret question you need to answer, or various hardware and software tokens (read more about it below).
- User’s biometric data. Iris, fingerprint, and face recognition.
- Items that a user owns. Hardware and software tokens, computer and mobile devices, bank cards, authentication devices.
Users need at least two methods of authentication to verify their identity with 2FA. The two elements are a combination of the above-mentioned verification options
What’s also important in establishing two-factor authentication to protect online accounts are the sign-in time and the location of the user.
For instance, when you want to sign into your email account from a different device or an unusual location, Google or any other provider asks for an identity check. Software solutions and payment processors are implementing these additional factors to increase the level of protection of their clients and reduce unauthorized access to a minimum.
Different Types of Two-Factor Authentication
We’ve already highlighted that the first element of two-factor authentication is a user password. The second factor in two-factor authentication is a piece of hardware or software tool that is in possession of the user.
Depending on the second verification factor, there are different types of two-factor verification:
Hardware Elements in Two-Factor Authentication
Before apps became so popular, some organizations used key fobs or smart cards as the second element of two-layer authentication.
In fact, some organizations still require their employees carry those hardware items with them when they’re entering their business premises. Today, however, they’re more frequently used as additional features of multi-factor authentication.
Text Messages as the Second Verification Factor
Banks, online payment processors, and other organizations rely on text messages as the second factor in their authentication process (in addition to passwords). It is the most practical option.
When a user wants to make an online payment, their bank sends them an SMS with a temporary code required to process the payment. There are two verification methods in this authentication, which ensures a high level of security.
Receiving access codes this way increases the risks of exposure to unauthorized access. Even though such codes are valid for only 5 or 10 minutes, this method of two-factor authentication is potentially hazardous due to offline threats.
Software Tokens for Enhanced Security
Generating software tokens via special apps is gradually replacing text messages as the second factor in the verification process.
Unlike codes sent to mobile devices as text messages, software tokens don’t include the offline environment; everything is happening online. They’re here to provide users with one-time passwords (OTPs) that are the real second factor in the authentication process.
When a user wants to access their bank or any other account, the system requests a one-time password. This temporary code is generated via a software token app and sent to the user. After that, the user enters it into the required field and gains access to their account. OTPs are usually valid only for thirty seconds or one minute at the most. When used or expired, the token ceases to be valid. As such, it reduces the possibility of unauthorized access or data theft to a minimum.
Push Notifications and Apps
It’s common today that organizations opt for two-tier authentication that consists of one software solution on a computer and one app.

For instance, when someone wants to confirm their access or authorization rights to the software, they receive a notification via a special app to approve access to the software in question. This notification is either in the form of a push notification or a PIN-code.
Biometric Elements in the Service of Authentication
Organizations have started implementing biometric elements as the second or even third factor of the authentication process.
Biometric payment cards are becoming more popular as a payment method. Instead of entering a PIN-code when we’re paying for a purchased item, we’re simply going to scan the tip of our fingers on a fingerprint reader on the bank card. Those cards will come with our fingerprints already integrated into them.

Additional biometric elements include scanning users' iris and faces. Our biometric data used for two or multi-factor identification are supposed to be stored only on your personal devices without being kept in databases. Hence, the risk of data theft is minimal.
ID chips are the next frontier in authentication technology. Instead of using hardware and software tokens, ID chips are inserted directly into the top skin layers. Even though this sounds futuristic now, the procedure is already used by some organizations to ensure secure access to business premises and data
Note: Learn about curl authentication, an authentication method where the server validates the provided credentials against a database of authorized users and serves the resources.
Benefits of Two Factor Authentication
Payment organizations and software-as-a-services providers are equally exposed to the risk of human error and brute force attacks. The following benefits of two-factor authentication make such outcomes less probable:
- Prevention of data and financial losses. If users’ accounts were protected only with passwords, hackers and data hijackers would have a much easier job of breaking those passwords. Likewise, if we didn’t use two-factor authentication, many users and organizations would experience severe data losses and, consequently, significant financial losses.
- Additional exterior security layer. Two or multi-factor authentication shelters online accounts with additional security layers. So, even if an unauthorized party somehow gets into possession of a password, obtaining the second factor is too complex a task for most of them.
- Identity and access management. Using another factor in addition to user credentials is a valuable addition to the identity and access management strategy of any organization. If these methods are used by employees working on delicate or confidential data, organizations considerably mitigate the risk of violating their clients’ personal or business data.
Therefore, two-factor authentication is a major security mechanism that ensures proper protection of organizations’ privacy and data policies.
Two-Factor Authentication and Credit Card Payments
The aforementioned authentication with SMS-codes is widely used by banks and other organizations. Software developers and compliance specialists working together on providing impenetrable protection solutions for financial institutions still find this the most user-friendly method.
For some clients who are not as tech savvy, credit card tokenization, additional apps, and OTPs are too complicated. Despite the hazards of a potential unauthorized access, the password-SMS combination is the most practical Venn diagram of available options.
Many banks and organizations operating credit card payments have already embraced push notifications for card payments via mobile phones. When a client wants to transfer funds using their e-banking account, their bank or payment company sends them a push notification to their cell phones, in addition to access credentials. This is both a user-friendly and secure option for clients to experience smooth payments without compromising their online security.
Note: Are you starting an online shop? Learn more about Payment Authentication Methods and Tools. Payment authentication is crucial for the protection of the buyers' personal information.
Conclusion
When organizations are considering the best options for their two-factor authentication process, they need to factor in their clients’ profiles. Opting for more advanced factors, like software tokens, is a reasonable option if their users are adept at using high-tech solutions.
Likewise, payment organizations with more traditional users are more likely to keep using text messages or simple push notifications to keep their clients protected. Learn more about 2FA in online payments and how to protect your customers
