Introduction
Customers regularly list security as their number one concern when paying online. Modern authentication methods and tools minimize fraud and protect all participants in the payment process.
At the same time, customers expect a quick, hassle-free checkout. A complex and heavy-handed payment flow always results in higher abandonment rates.
Learn about the best payment authentication methods and tools and strike the right balance between security and ease of payment.
What is Payment Authentication?
Financial institutions, payment processors, and merchants use payment authentication to ensure that a person’s data is not misused to make payments without their knowledge. A customer’s identity needs to be confirmed by verifying at least two or more independent elements.
In most cases, these elements fall into 3 categories:
- Something You Know - Information only the individual making the payment knows, for example, a password or PIN.
- Something You Have - An object a customer needs to confirm the purchase, such as a debit/credit card, USB token, smartphone, etc.
- Something You Are - A trait unique to an individual, including advanced technological solutions like fingerprints, retinal scans, voice recognition, etc.
An e-commerce website needs to incorporate several authentication methods and tools into the payment flow.
Payment Authentication Methods
Lax payment authentication methods increase chargeback and refund requests considerably. To maintain a good reputation with merchant banks and payment processors, you need to keep such claims to a minimum.
Choosing an authentication method and tool depends on a business model and laws and regulations in a country or region. Another factor is the ability to finance and technically implement advanced solutions.
3D Secure
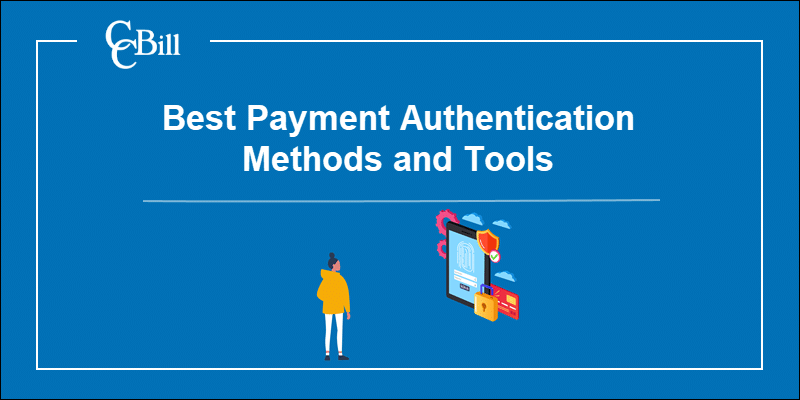
The 3D Secure protocol is one of the most widely used authentication methods for online payments. The three domains (3D) refer to the authentication performed by:
- The customer’s bank (card issuer).
- Payment acquirers such as payment gateways, merchant plugins, and banks receiving the payment.
- Directory servers, authentication history servers, and other interoperability solutions.
These three domains work together to cross-reference the data and confirm the identity of a customer.
Ordinarily, a customer needs to enter an OTP (One Time Password). The OTP is sent by the customer’s bank (or outsourced provider) using an SMS or Push notification. The notification is delivered to the phone number or email registered to the customer’s bank account.
Pros:
- 3D Secure is a strong authentication method as the customer needs to have their card details and access to their mobile phone to complete the payment.
- The OTP is valid only for a limited period and cannot be used for other transactions. As a result, the merchant or merchant bank does not need to store or protect long term customer passwords.
- 3D Secure has been around for many years. Even though it requires an additional step, customers are now accustomed to this authentication type.
Cons:
- Several verification systems working in conjunction increases the risk of technical failures, such as an undelivered SMS or unresponsive server.
- A customer might consider the process too complicated or fail to complete the transaction in the predefined timeframe. This leads to an increase in abandoned transactions.
3DS 2.0 involves contextual data sharing between a merchant and the card issuer. Historical data and risk factors are analyzed behind the scenes. As a result, the customer no longer needs to verify every transaction. An OTP or biometric scan, such as a fingerprint, is needed only for high-risk transactions.
Note: Sending out abandoned cart emails can help you regain lost transactions and customers. Check out our guide, to learn more.
Card Verification Value (CVV)
The Card Verification Value has become a pervasive authentication method for online card payments. Most payment processors require customers to enter their CVV code on the payment form by default.
The CVV code is a 3-digit or 4-digit code located on the back of a customer’s card. The code only works in conjunction with other details from the same card.
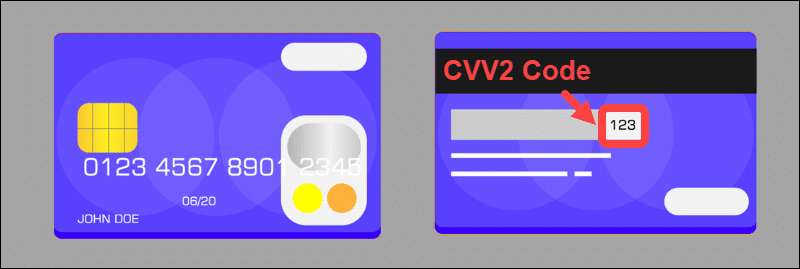
CVV2 is an advanced version of CVV that makes it harder to guess the combination of digits. Large card institutions have adopted the CVV2 standard.
Pros:
- Prevents online transactions without the correct CVV code.
Cons:
- This authentication method needs to be combined with other methods.
- Fraud is still a strong possibility if someone gets hold of the physical card or manages to copy card details, including the CVV code.
In some cases, a merchant can remove this requirement from their forms to improve conversion rates. This increases risk levels and is highly discouraged.
Address Verification Systems (AVS)
An AVS check compares the address a customer enters on the payment form with the address the customer’s bank has on file for the cardholder.
The AVS is useful as an indicator that there might be an issue with the transaction. Most non-face-to-face card payment processors use this method by default. Address checks focus on the numeric elements of the address, such as the ZIP/Postal code.
Pros:
- Address Verification Systems are effective and provide flexibility.
- Merchants can block transactions from particular addresses, regions, or countries.
- AVS allows merchants to review each declined payment and confirm if the issue is a result of fraud or a customer needs assistance.
Cons:
- Requires a lot of micromanagement.
- Strict rules can prevent payments due to minor address errors or typos.
Address verification systems need to be combined with other types of verification. Direct and personalized contact with customers is the best way to prevent fraud and build trust.
Note: Learn what happens in case of an AVS mismatch.
Geolocation
The location of the transaction, whether it is at an ATM, physical store, or IP address, provides useful information for authenticating payments.
Transactions made in two remote locations or different countries in short periods are suspicious. For example, an ATM transaction in Brazil followed by an online payment made in Japan only a few hours later is flagged and investigated by cardholder banks. They analyze each transaction and decide if it is necessary to contact the client directly and verify the transaction.
Pros:
- Merchants can block transactions from countries they deem to be more risk prone than others.
- The ability to block transactions based on IP.
- Payment processors can help you implement location restrictions with ease. Learn how to choose the best payment processor on the market.
Cons:
- Applying blanket rules can hurt sales figures if used in large and populous countries.
- It is necessary to analyze risk data regularly and adjust geolocation rules accordingly.
Applications have made it possible to match the transaction location with the GPS location of the customer’s smartphone. Even though this can be an effective solution, it has limited usage due to strict privacy regulations and customer preferences.
Web Verify
A CVV2 mismatch, AVS check, or purchases while traveling can trigger a declined payment even for valid transactions.
If payment is initially declined, it is vital to offer customers the option to complete the transaction. Depending on the reason and type of decline, payment processors provide numerous features and tools to verify the customer’s identity.
CCBill’s Web Verify is a straightforward and practical feature that ensures legitimate customers are not declined due to minor information discrepancies. Instead, they receive an email instructing them to contact CCBill’s 24/7 consumer support. Experienced representatives can then authorize and approve eligible transactions after confirming the consumer’s details.
Pros:
- Keeps strong verification in place while allowing customers to complete transactions that trigger fraud prevention systems.
- No additional costs involved.
Cons:
- A customer might decide to abandon the transaction if it fails initially.
Verification tools like Web Verify are a great way to build customer relations and mitigate offhand declines.
Behavioral and Risk-based Analytics
Behavioral analytics and risk-based authentication tools use big data and machine learning to survey and predict customer behavior. The collected data is used for marketing purposes, identifying customer purchasing patterns, and forming an effective security strategy.
For example, identifying behavior inconsistent with a customer’s purchasing history is a strong indicator of fraud.
Many small purchases from the same IP, purchases made from different IP addresses, and unusual payments involving large sums need to be closely monitored.
Pros:
- Risk-based authentication solutions are capable of pinpoint accuracy.
- High level of automation.
Cons:
- Very expensive to implement and maintain.
- The high costs outweigh the benefits for most small to mid-size merchants.
Behavioral authentication tools should become widespread and accessible to a larger number of merchants in the coming years.
Biometric Authentication
Biometrics is a highly secure and practical authentication method. Customers do not need to memorize credentials or fulfill additional authentication requirements. Pressing a finger or scanning their faces or voices grants access.
Smartphones have made this method available and popular with many customers. The preference for this authentication type comes from its ease of use.
Pros:
- It is difficult to falsify biological features.
- Customers seem to prefer biometric authentication.
Cons:
- Expensive to implement.
- Not globally widespread.
- Overhead costs for storing biometric data.
Biometric authentication solutions are expanding rapidly. New developments in the field are likely going to institute biometrics as a primary fraud prevention tool.
Trusted Payment Processor
A reputable payment processor with ample experience and developed mechanisms for fraud prevention is your best ally. Good payment processors provide most, if not all, the authentication methods mentioned above. Many are built into payment processor systems, so you do not have to implement or administer large fraud prevention departments and solutions.
You have the freedom to focus on how to incorporate the authentication process into the payment flow so that it is not too obtrusive for the customer.
By leveraging your knowledge about your customers and the payment processor’s experience with fraud prevention and risk management, you can create a safe and comfortable environment.
Age Verification
Regulators tend to increase authentication requirements for online retailers over time. Some countries (UK and Germany) already have legal requirements to restrict services and products to specific age groups.
Age verification is part of a broader online child protection policy and focuses on adult content and online gambling platforms.
The age verification process mandates merchants to confirm the customer’s age. Merchants usually ask customers to provide copies of personal IDs. As expected, this severely impedes the payment flow and leads to payment abandonment.
Third-party solutions and services, such as AgeChecked, can help prevent churn and ensure only customers of appropriate age have access to particular products.
Payment Tokenization
Tokenization is when sensitive information, like payment details, is replaced by a unique and random string of characters called a token. The token has no logical connection to the information it represents and cannot be reversed or decrypted to access the sensitive information.
Transferring and storing tokens instead of payment information offers an exceptional level of security. Even if a breach takes place, it is impossible to deduce banking details from the token.
Merchants can store tokens of their customer's payment details and allow them to make multiple purchases without re-entering the details. Subscription businesses use tokens to increase conversion rates by offering upgrades and one-click payments.
Tokens facilitate a seamless payment flow and encourage customers to buy products in shorter intervals.
Note: Read our article How Does Payment Processing Work to learn about the participants in the system and the stages of the payment processing.
Conclusion
You now have a good understanding of authentication methods and tools, including their strengths and weaknesses.
Implementing multiple sophisticated tools is expensive. Fortunately, well-established payment processors and banks provide authentication tools and services to merchants. These large institutions have more resources and are better equipped to prevent online payment fraud.
Our suggestion is also to learn more about 2FA in online payments and how to protect your customers.
