Introduction
A security breach on an ecommerce website may cause an irreparable loss of customers, revenue, and reputation.
The number of sophisticated security threats is increasing, and so is the number of methods used to combat them. It’s challenging to develop a comprehensive strategy and decide which security practices to prioritize.
Small and mid-sized ecommerce merchants cannot afford to invest in expensive security tools, features, and staff. However, even businesses with limited resources can create a safe shopping environment for their customers.
Note: Reliable payment processing for ecommerce is crucial. Find a reliable partner that handles customer data with care.
Read on to find out how to apply the best security practices and keep your ecommerce store secure.

Ecommerce Security Best Practices
Combating fraud does not need to be expensive and time-consuming. Certain practices have proven to be effective without significantly increasing costs or requiring constant monitoring.
Employ the following practices to improve security:
- Spend time and effort to train staff.
- Develop rigorous internal security procedures.
- Use third-party software solutions, like plugins, to enhance store security.
- Rely on and closely cooperate with other participants in the payment process.
Keep in mind that even advanced software solutions may not be able to detect fraud in advance. Try to establish processes that limit the damage once an attack occurs.
1. Employee Training
Predictable patterns in human behavior represent the weakest link in security infrastructure. Training staff regularly minimizes the threat of a breach caused by human error.
Employees should understand how some of the most common threats work and how their behavior might assist or prevent these attacks.
- Require staff to follow strict fraud prevention procedures.
- Provide access to relevant training courses and regularly update the material to reflect recent developments in fraud prevention.
- Analyze employee reactions to simulated and actual attacks and adjust procedures accordingly.
Employees need to know what to do once an attack is underway, how to respond when customers report different types of fraud, and how to deal with the aftermath of a successful attack. Well-trained employees can react quickly and control the damage caused by fraudulent activity.
2. Use Strong Passwords
Users with access to essential store systems must use strong passwords or passphrases. Use an extension or plugin to implement two-factor authentication for employees. Only the most sophisticated attacks are able to bypass this type of authentication.
Forcing customers to use overly complex passwords is not a viable solution for ecommerce stores.
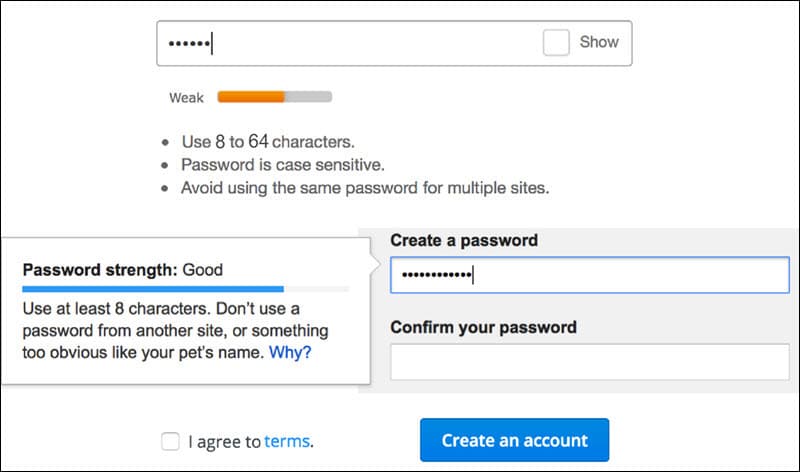
Implement a customer-facing password policy that includes:
- A minimum password length requirement with reasonable complexity rules (8 to 64 characters).
- Account lockout after several incorrect login attempts.
- A blocklist that prevents the use of dictionary terms, usernames, names of website services, and compromised passwords.
Creating a balanced password policy that addresses security concerns and does not negatively impact customer experience is difficult. Use these password policy practices for ecommerce websites to set up the best possible policy for your online store.
3. Implement HTTPS
An SSL (Secure Socket Layer) certificate establishes an encrypted connection between the store’s server and the user’s browser. The certificate guarantees a secure transfer of data and can considerably reduce the risk of man-in-the-middle attacks.
Man-in-the-Middle Attack - An attacker compromises the communication channel between the store’s server and customer. By monitoring and intercepting the transfer of data, they can collect valuable information or propagate malicious files and software.
SSL certificates are issued by Certification Authorities (CAs). The cost of the certificate depends on the level of validation and the number of domains and subdomains to which it applies.
Organization Validated SSL certificates are more expensive, and the validation process can take longer, but they provide enhanced fraud protection.
Check if your web host offers SSL certificates as part of their pricing plan. A web host can also help reduce costs by managing the installation of the SSL certificate.
4. Backup and Restore
Regular backups protect your store from malware, ransomware, and other attacks that limit availability or destroy valuable data.
An advanced backup system saves the state of an entire ecommerce store at regular intervals. The copy is safely kept offsite and used to restore the original data if anything happens to the primary location. Keep in mind that it takes time to retrieve the latest copy and deploy it in a working environment.
Backing up an entire system consumes lots of resources and can't be executed every second of every day. Losing some data is acceptable compared to the irreversible loss of essential information due to a security breach.
Note: Learn how to back up and restore Magento using several different methods in our article Magento Backup and Restore Tutorial.
5. Use Secure Payment Processing
Advanced software solutions designed to prevent fraud are often too expensive for most ecommerce.
An established payment processor has ample resources and can invest in payment validation tools like 3D Secure and velocity control software. They also employ security experts with the knowledge and experience to protect your business from even the most sophisticated attacks.
Choosing the right payment processor should be a result of careful deliberation to ensure that your business model is adequately supported by the features they offer. New merchants can avoid high initial costs by working with payment processors that use percentage-based pricing.
6. Regular Software Updates
Outdated software is a serious security threat. Attackers are vigilant and actively seek out systems that do not apply security patches and fixes. It is not enough to keep core systems up to date; plugins and third-party solutions must be reviewed and updated regularly.
Take particular care when updating plugins and custom software and ensure that the compatibility with other systems is maintained at all times. Test extensively after every upgrade and identify vulnerabilities from the start.
7. Ecommerce Security Plugins
Depending on the store’s platform there may be hundreds of extensions that focus on particular security features. Always install plugins from official pages or trusted sources.
Explore available solutions before committing to a single plugin. Use reputable online resources to learn about industry trends and identify the most popular security plugins.
Many plugins have free versions that may provide enough functionality to meet your store’s requirements. Some of the essential security features and tools include:
- Blocking IP addresses
- Address verification systems (AVS)
- Geolocation
- Adding CAPTCHA
- Age verification
Only install plugins that bring actual value to the security system. Having too many plugins can quickly become difficult to manage and slow your system down.
8. Customer Support
The customer is often the first person to notice and report fraud. An ecommerce merchant needs to be ready to assist the customer and react accordingly. The reported issue may only be an indicator of a broader breach. Your first step is to protect the customer and then determine if other customers are affected. Coordinate with the payment processor and card issuer to investigate thoroughly.
Customer support service is on the front line, and their initial reaction is vital for containing the damage to your brand and business.
Note: Stay up-to-date with the ecommerce fraud trends in order to combat fraudulent behavior more efficiently.
9. Reduce the Attack Surface
An ecommerce website should only collect data required for the checkout process. One of the most successful methods to combat fraud is not to store customer payment information. If the information is not available on any of your systems, the incentive for a potential attack is absent.
The tokenization of payments has helped reduce the attack surface for ecommerce stores. If an attacker manages to get hold of a customer’s token, the damage is contained to a single website.
10. Two-Factor Authentication (2FA)
Implementing two-factor authentication is simple and highly effective in preventing fraud. Most attack vectors are rendered ineffective by two-factor authentication.
Content management systems provide numerous plugins with user-friendly interfaces and features. For example, installing two-factor authentication in WordPress is a quick and straightforward process.
Using 2FA to verify customer payments may disrupt the payment flow and increase abandonment rates. Merchants with high-risk businesses should seriously consider implementing this type of verification. Customers are getting used to 2FA and beginning to appreciate the added security.
Using 2FA to verify employee logins is becoming an industry standard, and all ecommerce merchants should implement this feature.
11. Use a Secure Web Hosting Service
The web hosting service needs to have experience with ecommerce security and proactively work to mitigate potential risk.
Choose a web host that adds value and introduces additional security layers on top of the security measures you already have in place.
Check if the web host performs regular risk assessments and exercises in information assurance.
12. Vulnerability Tests
Regularly testing your system for security flaws helps discover and fix issues before an attacker exploits them. The test should not be limited to IT and technical solutions, but also include staff response and the effectiveness of the procedures in place.
A system-wide vulnerability assessment can take place annually or in a limited capacity when adding new services or hardware. The test results and subsequent analysis should identify possible improvements to the existing system.
Using employees to test for vulnerabilities is cost-effective, but potential issues are more likely to surface when using a specialized third-party service.
13. Restrict Access with User-Defined Roles
Ecommerce stores with multiple employees need to define specific roles and restrict access to systems relevant to those roles. For example, there is little reason for a salesperson to access the CMS backend. In addition, whitelist specific IPs for users to block access from all other addresses.
This security measure prevents attackers from escalating their access and propagating their activity to other parts of the system.
14. Fraud Response Plan
Regardless of the level of preparation, an ecommerce website is going to be affected by fraud. Much of the fraudulent activity occurs outside of the store's scope, and the merchants can't prevent it.
It is essential to have a clear plan on how to proceed once you become aware of malicious activity. Coordinate with all the other participants in the payment process. Take steps to block the activity if possible. Get in touch with the payment processor and the card issuer so they can take appropriate measures from their side.
Investigate the issue to find out if it is an isolated incident or a broader issue. Your aim is to protect your business and the customer and stop the fraud from escalating any further.
Common Ecommerce Security Threats
A vulnerability is a potential foothold that allows unauthorized users to escalate access to other core systems. An attack aims to steal sensitive business and customer data, disrupt store operations, or demand payment to unblock critical services.
Ecommerce stores are also highly exposed to fraud committed using genuine customer data. Attackers acquire customer information through social engineering or by purchasing stolen credentials. The data is used to take over existing accounts, create fake accounts, and make fraudulent purchases.
Unauthorized individuals use several attack vectors to accomplish their goals. Ecommerce stores encounter security threats every day.
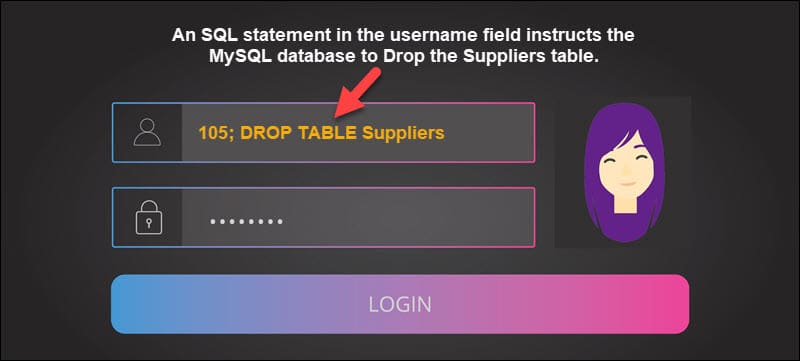
The most common ecommerce security threats are:
- DDoS Attacks (Distributed Denial of Service) - Automated tools coordinate and send excessive traffic to the target’s servers. The aim is to overwhelm the ecommerce store’s systems and render them unavailable to customers and administrators. The attackers threaten to escalate the denial of service and ask for payment to stop further attacks.
- SQL Injection - An SQL statement is placed in a field intended for customer input, such as the password field or search bar. The web application sends the SQL query to the designated database. The query is processed by the database and may result in the attacker extracting data or gaining control over the database.
- Cross-Site Scripting (XSS) - An attacker manages to insert malicious code into the legitimate website’s code. Once the customer visits the website, the script is delivered to the customer’s browser. The software then collects information from the customer’s system, browser, cookies, etc.
- Brute Force Attacks - Automated scripts try to guess a customer’s username and password and log in to their account. The software uses lists of dictionary words, common password variations, or data collected from a previous breach.
- Social Engineering - Social engineering is a complex attack vector that has several phases. An attacker gathers information about the victim, initiates contact, and tries to establish a relationship. They try to exploit that relationship to collect sensitive payment data or extract direct monetary gain.
- Spam - Unsolicited marketing messages on your website can damage the store's reputation by misleading and confusing customers. For example, fake user accounts are used to place links in the comments section of a website. These links may lead customers to potentially fraudulent pages, advertise illegal services, or spread malware.
- Phishing - An attacker contacts a victim and poses as a person or company they know and trust. The objective is to persuade the victim to provide sensitive information, such as login credentials and payment details. Frequently, attackers request direct payments or ask users to click on links that activate malicious software.
- Account Takeover Fraud - Unauthorized individuals access a customer’s account, change vital account details, and make fraudulent purchases.
- Malware (Trojans, Ransomware, Drive-by Attacks) - Malware tries to remain undetected while it infects and spreads throughout the target system. Trojans are a type of malware designed to appear as useful software and convince the victim to install it willingly. The installed software may block access or threaten to delete valuable data on the victim’s system. Without a backup, the only way to retrieve the data is to pay the ransom. There are no assurances that the information is going to be returned.
- Financial Fraud (Identity Theft) - Stolen customer data is used to create new accounts, sign legally binding contracts, or conceal other illegal activities.
Customers rely on ecommerce merchants to protect their personally identifiable information. Ensure that your store’s core services are secure by applying best practices and tools.
Conclusion
Use this comprehensive list of security features to make your ecommerce website and customers safer. Do not hesitate to implement several or all of the listed security features and practices as they do not require significant investment or technical expertise.
Advanced payment authentication methods and tools are slowly becoming available to a wider number of ecommerce merchants. These tools help merchants create a secure online environment.
