Introduction
Merchants, banks, and payment processors need to share and authenticate payment information. Unprotected data is susceptible to theft while being transmitted and stored during the payment process.
Encryption and tokenization significantly reduce data exposure and keep cardholder information safe.
Learn about the differences between tokenization and encryption and how they protect your customers and your reputation.
Tokenization vs. Encryption in a Nutshell
Tokenization replaces a piece of information, such as a credit card number, with a random and unrelated set of characters called a token. A token does not hold any information and has no value to individuals looking to commit fraud.
Encryption uses an algorithm to encode sensitive payment information. The intended recipient of the data uses a cryptographic key to decrypt and read the information.
How Does Tokenization Work?
Tokens are well suited for payments initiated from mobile devices. Digital wallet apps, such as Google Pay, Apple Pay, CCBill Pay, Alipay, and others, use tokens to allow customers to pay without re-entering their payment information. For example, a tokenization process initiated from a digital wallet consists of 10 steps:
1. A customer installs a digital wallet app on their device and enters their card information.
2. The digital wallet app sends a provisioning request to a Token Service Provider (TSP).
3. The TSP validates the card credentials with the customer’s bank.
4. The TSP creates and stores the PAN-Token correlation in its highly secure token vault.
5. The token is provided to the digital wallet app.
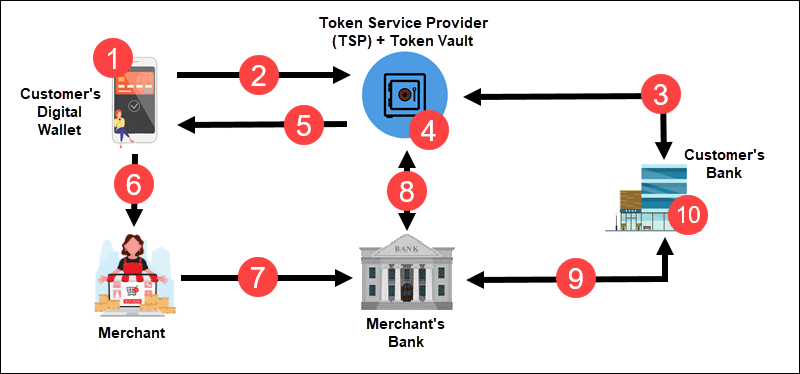
6. The customer pays using the digital wallet token.
7. The merchant forwards the token to their bank for validation.
8. The merchant’s bank asks TSP to provide the PAN related to the token.
9. The acquiring (merchant’s) bank validates the PAN with the customer’s bank.
10. The customer’s bank authorizes the transaction.
The TSP and cardholder’s bank continue to manage the token through its lifecycle. Merchants no longer need to use or store sensitive cardholder information. Instead, the TSP, banks, and third-party payment processors perform verification and validation processes.
How Does Encryption Work?
Merchants must secure the transfer of information between a card terminal or payment form and a remote payment processing system. Encryption protects sensitive information by applying an advanced mathematical algorithm.
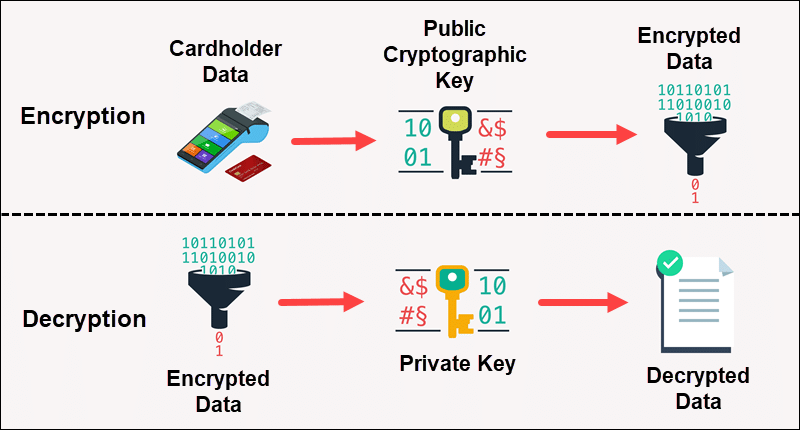
Environments with many interlinked participants, like a payment process, use asymmetric encryption. This type of encryption utilizes two different cryptographic keys.
Organizations sending data use a public key to encode customer information before sending. The intended recipient has a private key to decrypt and access the information.
For example:
1. A customer makes an in-store payment.
2. The merchant’s payment terminal uses a public key to encrypt the customer’s data.
3. The encrypted data is sent to the payment processor.
4. The payment processor uses a private key to access the data and validate the payment with the card issuer.
If someone compromised the encryption key, they would only have access to data encrypted with that specific key. You can limit the amount of data being encrypted with a single key by rotating multiple encryption keys.
Data Encryption vs. Tokenization Side by Side Comparison
Tokenization and encryption use two distinct approaches to secure sensitive data. The following table provides a quick comparison between tokenization and encryption.
| Features | Encryption | Tokenization |
|---|---|---|
| Security | A proven security method that allows access to data only once it is decrypted. | It is not possible to extract sensitive data from a token, making it a robust security method. |
| PCI Compliance | Mandatory for PCI security standards compliance. | Not a PCI requirement but does reduce the scope of PCI reviews. |
| Use Cases | Protects data transfer over insecure networks and secures data storage. | - Digital Wallets - Recurring Payments - In-App Payments - Pay Buttons |
| Data Type | Unstructured and Structured Data. | Only Structured Data. |
Encryption is an indispensable component of payment processing. Tokenization enhances data security and introduces new features that improve customer experience and drive sales.
Security of Tokenization vs. Encryption
Encryption is an essential and reliable component of payment processing. Accessing encoded data without a key is a laborious effort that nearly always fails. Using asymmetric encryption with regularly rotating keys is vital for protecting payment information.
A token is a substitute for the information it represents. Participants in the payment process do not need to handle credit card information directly. Storing tokens is much more secure than storing encrypted primary account numbers (PAN).
A single PAN can be used to create multiple tokens. A device-specific or merchant-specific token establishes an additional security layer. It is possible to deactivate a compromised token in real-time with minimal impact for the customer. The customer only needs to create a new token without replacing their card or primary account number.
PCI Compliance
Even though credit card data is encrypted, extensive security infrastructure is still necessary. PCI compliance guarantees the safety of payment information by forcing organizations to apply strict payment industry standards. Fulfilling PCI encryption standards requires a lot of resources and can drive up operating costs significantly.
Tokenization is not a PCI compliance requirement but is considered an established practice in payment processing. As merchants do not handle payment information directly, tokens reduce the scope of PCI compliance reviews. Hence, this process decreases the associated costs.
Use Cases of Tokenization and Encryption
Sharing payment information over exposed networks and storing credit card data would be unfeasible without encryption. For example, a POS terminal or an ATM could not safely communicate with remote systems and validate card information.
Besides the security benefits, tokens can be used to drive sales. Customers utilize their tokenized information to pay without using a credit card or entering personal data.
For example:
- Digital Wallet - A customer can create a token and use a mobile device or wearable, like a smartwatch, to purchase goods or pay for services.
- Recurring payments - Merchants and e-commerce platforms store customer tokens to initiate recurring payments without accessing or storing credit card details.
- In-app payments - Customers can pay using mobile applications without exiting or closing the app.
- Pay buttons - Merchants can place pay buttons on their websites, allowing customers to pay using previous tokens.
Find out more about the benefits of tokenization in our post What Is Tokenization in Payments?
Structured vs. Unstructured Data
Tokenization is best applied to structured sets of data. Tokens are a perfect fit for personally identifiable information such as a PAN, social security number, phone number, or email.
You can encrypt any file, regardless of its content or structure. This means that encryption can be used to secure both credit card data and sizable unstructured data files. Encryption is highly efficient. A small cryptographic key provides access regardless of the file’s size.
Conclusion
The article provided the main differences between tokenization and encryption and evaluated the advantages they bring to your business.
These two methods are not mutually exclusive. To get the best results and improve data security, use both tokenization and encryption side by side.
