Introduction
Ecommerce websites use personalized customer accounts to streamline payments, offer discounts, and set up loyalty programs. If an unauthorized individual takes over a customer’s ecommerce account, they can exploit these features to make illicit transactions.
Account takeover fraud (ATO) severely impacts customers and has a knock-on effect on chargeback levels and brand reputation.
Learn how Account Takeover Fraud works and how to protect customers and your ecommerce business.

What is Account Takeover Fraud?
Account takeover fraud (ATO) occurs when an attacker manages to access a legitimate user account. The attacker uses that access to collect personal and payment information, change account details, or initiate transactions posing as the account owner.
An account takeover becomes identity theft if the access is used to open new accounts, request credit cards, or ask for bank loans.
This ecommerce fraud trend is difficult to uncover as attackers maintain normal usage patterns and stay undetected for long periods. Customers first realize that they were victims of account takeover fraud once their account is no longer accessible or see unfamiliar charges on their bank statements.
Note: Learn more about ecommerce fraud and types.
Account Takeover Targets and Goals
The goal of account takeover fraud is to acquire illegal monetary gain. The majority of ATO attempts target accounts that allow users to make purchases, transfer funds, or contain sensitive personal data.
Typical targets for account takeover fraud include:
- Email Accounts.
- Social Media Profiles.
- Online Banking Accounts.
- Customer Accounts (eCommerce).
- Business models that utilize password-protected areas.
Attackers always look to escalate access by targeting several accounts belonging to the same person. For example, taking over an email account serves as a gateway to access that individual’s ecommerce account.
Account Takeover Fraud in Ecommerce
Customer accounts, one-click payments, and loyalty programs are sure ways to increase profit margins. However, these features have made ecommerce websites a prime target for account takeover fraud. The types of ATO fraud ecommerce merchants are most likely to encounter include:
- Bank Account Fraud - Clients use their online banking accounts to initiate transactions, ask for bank loans, add authorized signers, and request new credit cards. If an unauthorized user gains access to such an account, they would have the same capabilities. Ordinarily, attackers lock out the account owner and transfer funds or purchase products on ecommerce websites using non-credit card payment methods.
- Credit Card Fraud - Purchases made with stolen credit card information are a constant threat to ecommerce stores. Websites that allow return customers to store payment details and reuse them for subsequent purchases are especially at risk. Unauthorized individuals can pay from the customer’s account and no longer need the actual credit card information. Merchants offering one-click payments need to closely monitor customer accounts and introduce two-factor authentication to verify account information changes.
- Loyalty Fraud - The majority of ecommerce merchants offer discounts and loyalty programs to return customers. The points awarded in loyalty programs are an ideal target for account takeover fraud. Merchants tend not to implement strict validation systems for spending loyalty points. These transactions go under the radar of banking and financial organization and make it much easier for attackers to hide their activities.
Account takeover fraud does not only result in the loss of reputation and shipped products. Merchants often need to reimburse fraud victims and pay fees associated with the subsequent refund and chargeback requests.
How Does Account Takeover Fraud Happen?
To take over an account, an attacker employs a set of techniques in several distinct stages:
- An unauthorized individual acquires bundles of personal information, login credentials, emails, or phone numbers. This stage usually involves purchasing information from criminal sources. But the information can also come from man-in-the-middle attacks, phishing campaigns, social engineering, etc.
- If the information is user and service-specific, for example, comes from a company breach, an unauthorized user can simply log in. Attackers also use automated systems to test large numbers of credentials against login pages until they successfully access an account (credential stuffing).
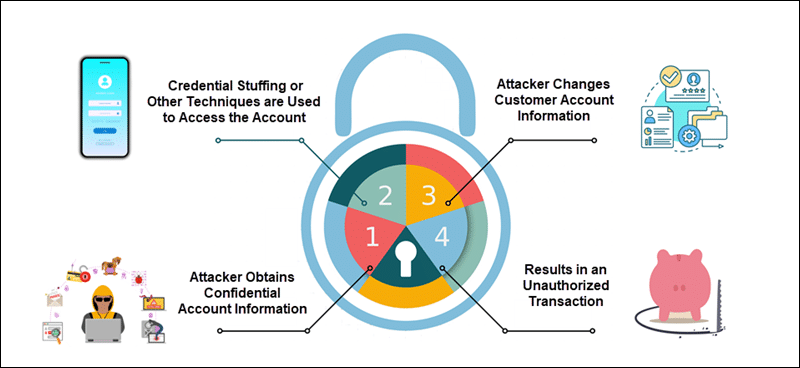
- Once they gain access, attackers try to modify account information, for example, contact emails, phone numbers, passwords, PINs, etc. Most services require additional authentication to change account details, such as email verification. However, by this stage, sophisticated attackers may already have access to the customer’s email account or have the means to intercept calls or push notifications.
- If an unauthorized individual manages to change account details, they have taken over the customer’s account and can make transactions and payments.
What Are Common ATO Fraud Techniques?
Some of the most commonly used account takeover attack vectors include:
- Phishing - Phishing methods are very successful in both mass data collection and highly targeted attacks. Fraudulent emails, URLs, and websites are used to spread malware and harvest personal and payment information.
- Credential Stuffing - Most users tend to recycle their credentials and use them to access several accounts. Automated credential stuffing attacks use lists that contain genuine usernames and passwords. They avoid account lockouts by attempting to match only one password to each username. These attacks are more advanced than Brute Force attacks, where automated scripts attempt to guess usernames and passwords using dictionaries and common passwords and their variations.
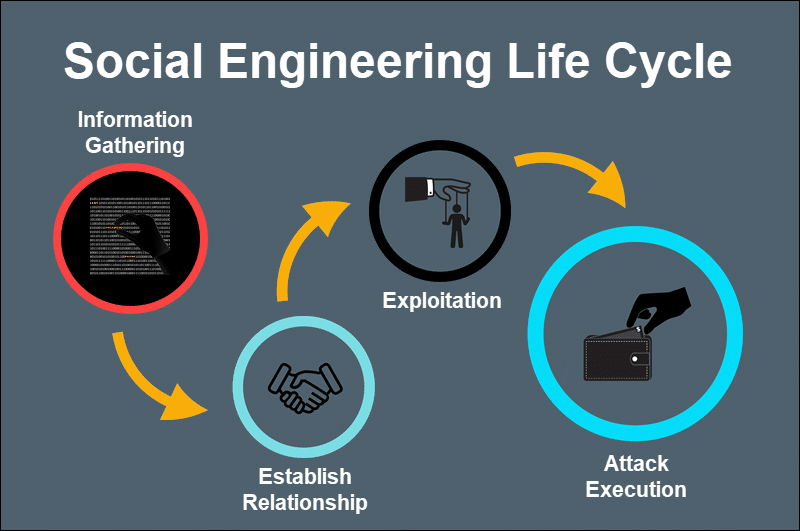
- Social Engineering - Social Engineering attacks are a set of sophisticated and complex actions that trick the account owner into providing their sensitive personal data willingly. These methods include scareware, pretexting, or quid pro quo vectors.
- Man-in-The-Middle Attacks - An attacker manages to place themselves between the victim and the genuine website. For example, setting up a copy of the original website and using it to collect sensitive customer information.
How to Prevent Account Takeover Fraud?
Investing in expensive software solutions to mitigate risk levels is not viable for most ecommerce stores. Ecommerce merchants need to establish strong password policies on their websites. The following features and processes help slow down attackers and limit the damage caused by account takeover fraud:
- Proactive Monitoring - Identify ATO fraud attempts before they breach your system. Keep track of multiple login attempts, suspicious IP usage patterns, a surge of purchases from specific countries and regions, etc. Track large orders and always check if there were any account information changes before such orders took place.
- Two-Factor Authentication (2FA) - Merchants are concerned that Two-Factor Authentication impacts customer experience negatively. However, using 2FA systems to verify personal and account information changes reduces the risk of account takeover fraud considerably. Only the most sophisticated attacks are able to circumvent 2FA.
- Supervise Loyalty Programs - Track the spending of loyalty points on your website and apply the same level of scrutiny as with regular transactions. A customer that changes their account details before spending loyalty points should prompt you to investigate the transaction in more detail.
- Tokenization - Tokenized payments do not prevent account takeovers. If a token is compromised, the payment information cannot be reused for other accounts, and the damage is easily contained. Tokenization keeps the customer’s personal payment information safe and increases customer trust substantially.
Ecommerce merchants, banks, and payment processors need to work together to share information and the know-how to protect customers. Regularly communicate with your payment processor to help develop practices that can prevent ATO fraud and keep your chargeback levels in check.
Conclusion
You now know how ATO fraud happens and understand its main objectives. Use this knowledge to develop a sound and effective strategy for preventing account takeover fraud.
New developments such as tokenization and biometrics are going to make the payment process safer, but it is essential to stay one step ahead.
